Wi fi wpa2
Data: 3.03.2018 / Rating: 4.6 / Views: 822Gallery of Video:
Gallery of Images:
Wi fi wpa2
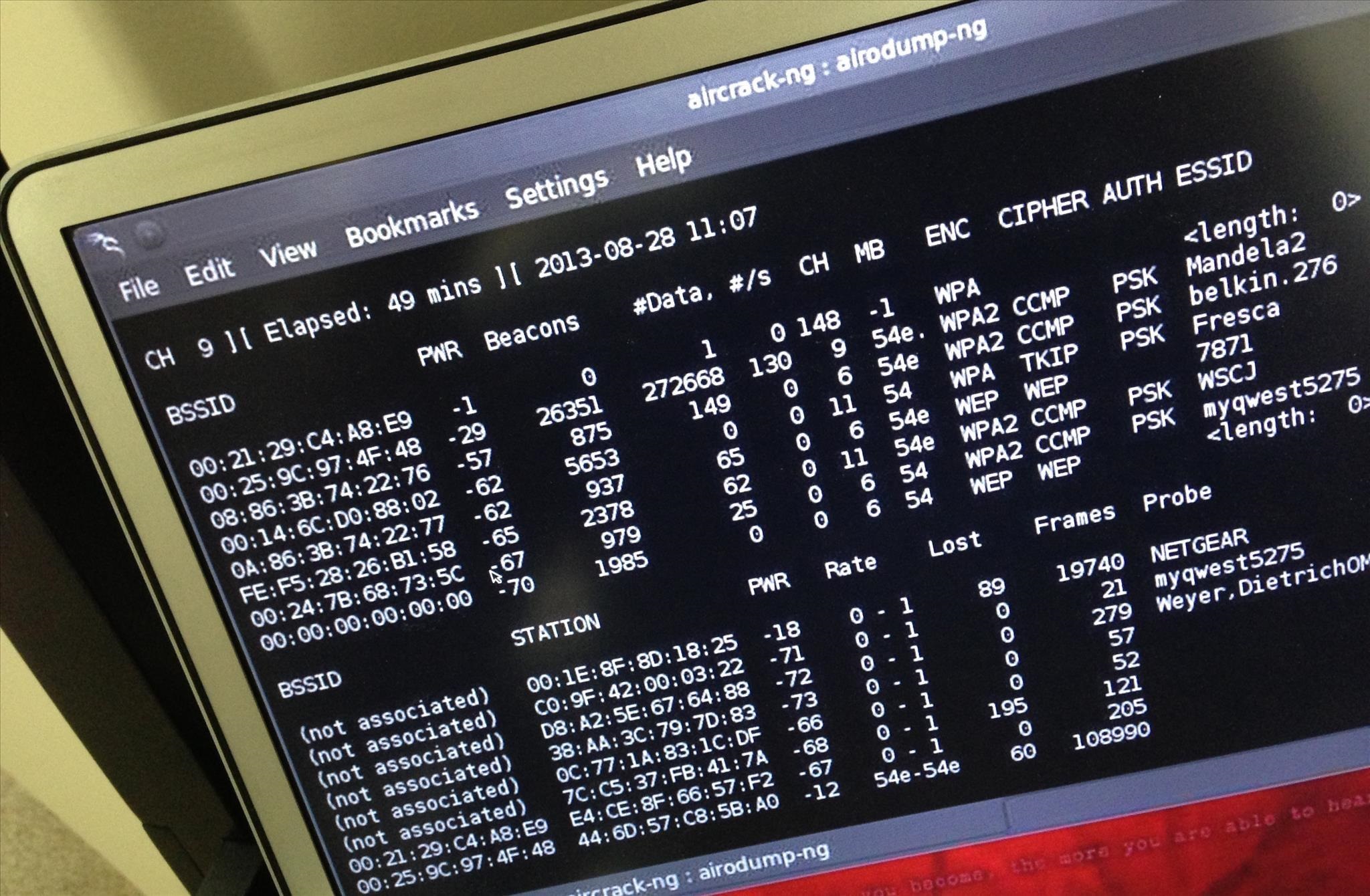
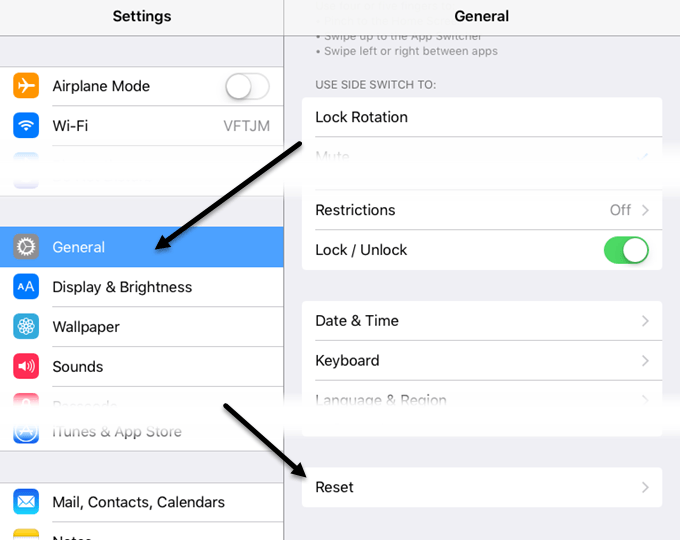
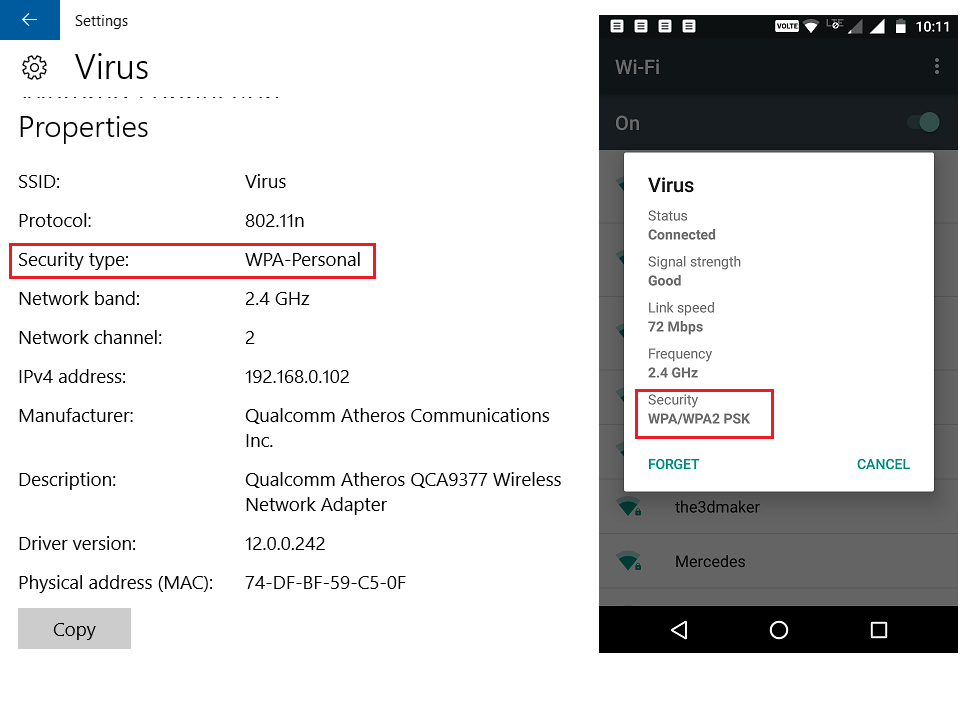
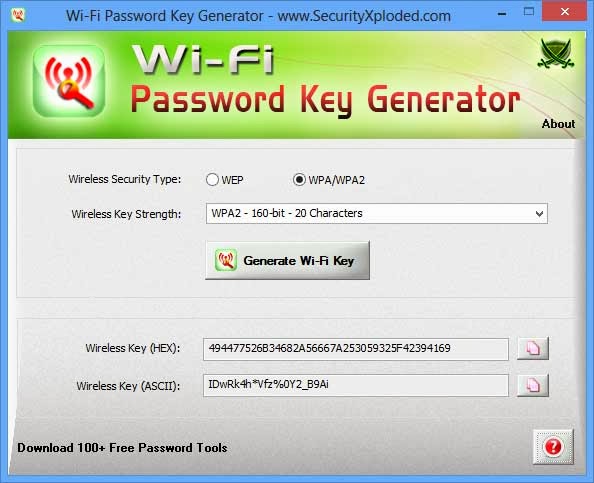
wpa2 (aes) wifi WPA2. WiFi encryption developed yet another chink in its armor this week. Its now much easier to grab the hashed key. Its now much easier to grab the hashed key. So a hacker can capture a ton of WPA2 traffic, take it away, and decrypt it offline. wpawpa2wpa3 WPA2 is a popular standard used to set up WiFi networks and is most commonly used to authenticate users with a password but can also handle more sophisticated authentication schemes using usernames, certificates, and private keys. WiFiWPA2 WiFi Protected Access (WPA) was the WiFi Alliances direct response and replacement to the increasingly apparent vulnerabilities of the WEP standard. WPA was formally adopted in 2003, a year before WEP was officially retired. As a replacement, most wireless access points now use WiFi Protected Access II with a preshared key for wireless security, known as WPA2PSK. WPA2 uses a stronger encryption algorithm, AES, that's very difficult to crackbut not impossible. Secure WiFi networks are passwordprotected and have by their names. Go to Settings WiFi, and make sure WiFi is turned on. Tap the name of the secure WiFi network you want to join. Enter the password for the secure WiFi network, then tap Join. WPA2 WiFi routers support a variety of security protocols to secure wireless networks: WEP, WPA and WPA2. However WPA2 is recommended over its predecessor WPA (WiFi Protected Access). However WPA2 is recommended over its. WiFi Protected Access security sees strong adoption: WiFi Alliance takes strong position by requiring WPA security for product certification. Weakness in Passphrase Choice in WPA Interface, by Robert Moskowitz. The folks behind the passwordcracking tool Hashcat claim they've found a new way to crack some wireless network passwords in far less time than previously needed. Jens Steube, creator of the open. We discovered serious weaknesses in WPA2, a protocol that secures all modern protected WiFi networks. An attacker within range of a victim can exploit these weaknesses using k ey r einstallation a tta ck s (KRACKs). The WiFi Alliance maintains an online database of products that is somewhat difficult to use. Go to their Web site, check the WPA2 box and then select which vendor you are interested in. Crack WPAWPA2 WiFi Routers with Airodumpng and AircrackngHashcat. This is a brief walkthrough tutorial that illustrates how to crack WiFi. lan wifi aes WPA2AES The WiFi alliance announced the release of WPA3 in January, which presented a new standard of WiFi security for all users. WPA3 uses individualized data encryption, protects against bruteforce. A computer with WiFi and a DVD drive. BackTrack will work with the wireless card on most laptops, so chances are your laptop will work fine. However, BackTrack doesn't have a full compatibility. WPA2 protocol used by vast majority of wifi connections has been broken by Belgian researchers, highlighting potential for internet traffic to be exposed Security researchers 1 have discovered a major vulnerability in WiFi Protected Access 2 (WPA2). WPA2 is a type of encryption used to secure the vast majority of WiFi networks. A WPA2 network provides unique encryption keys for each wireless client that connects to it. WiFi Protected Access 2 (WPA2) As the successor to WPA, the WPA2 standard was ratified by the IEEE in 2004 as 802. Like its predecessor, WPA2 also offers enterprise and personal modes. WiFi Protected Access 2 is the current industry standard that encrypts traffic on WiFi networks to thwart eavesdroppers. And since it's been the secure option since 2004, WPA2 networks are. Most WiFi products bought in 2005 or after should support WPA2. If you have a wireless router, access points, computers, or other WiFi devices that were purchased in 2005 or before, you might. WiFi Protected Access 3 or WPA3, for short is an improved wireless security protocol designed to make it more difficult for criminals to hack a wireless network. This note is meant to inform that a serious vulnerability affecting the WiFi Protected Access II WPA2 protocol has been discovered, presents the repercussions of a potential attack and offers basic security recommendations. On October 16, 2017 security researchers disclosed highseverity vulnerabilities in the WPA2 Protocol that would make it possible for attackers to eavesdrop WiFi traffic passing between computers and access points. Since 2006, all WiFi certified products must use WPA2 security. If you're looking for a new wireless card or device, make sure it's labeled as WiFi CERTIFIED so you know it complies with the latest security standard. TKIP and AES are two different types of encryption that can be used by a WiFi network. TKIP is actually an older encryption protocol introduced with WPA to replace the veryinsecure WEP encryption at the time. 11iWPA2 (WiFi) WPA The flaw in WPA2 was discovered by Mathy Vanhoef, a postdoc security researcher in the computer science department of the Belgian university KU Leuven. Until just a few days ago, many security experts felt the WPA2 encryption standard was uncrackable. This popular standard, used on everything but home WiFi routers to the sophisticated security equipment used by multinational corporations, was considered the gold standard in the industry, but that invincibility has recently been shattered. 11acWiFi auWiFiau WiFi SPOT wpawpa2, wep ( wep, wep wifi wifi wps. However, the aging WPA2 standard has no such protection. According to the researcher, the new attack method does not rely on traditional methods used to steal WiFi passwords. WiFi Protected Access 2 is a network security technology commonly used on WiFi wireless networks. It's an upgrade from the original WPA technology, which was designed as a replacement for the older and much less secure WEP. WiFi detector Short for W iFi P rotected A ccess 2 P re S hared K ey, and also called WPA or WPA2 Personal, it is a method of securing your network using WPA2 with the use of the optional PreShared Key (PSK) authentication, which was designed for home users without an enterprise authentication server. WPA2 continues to provide security and privacy for WiFi networks and devices throughout the WiFi ecosystem. WPA2 devices will continue to interoperate and provide recognized security that has been its hallmark for more than a decade. WiFi Easy Connect enables the utilization of another device with a more robust interface, such as a smartphone or tablet, to provision and configure devices by
Related Images:
- Jonas brothers single
- Zero 7 2012
- Best of road trip
- The the 1993
- Charlies Angels Full Throttle 2003
- Scott pilgrim vol 1
- 99 women 1969
- Legend of korra skeletons
- Black sabbath mkv
- Apple Imac 20 Inch Early
- Iron giant 1080
- 13th warrior avi
- Motley crue live concert
- Rainbow six vegas 2 ps3
- Taken 2 2012 1080p
- Continuum s03e12 1080p
- Money talk 2011
- A secret history of civilisation
- Half life server
- Belle sub nl
- Trap remixes 2014
- Pack of lies
- El seor de los cielos 2
- The time machine 720p
- Spartacus s03e02 720p hdtv
- Whos your daddy 14
- Sonic the hedgehog xbox360
- Brothers and sisters s02e01
- Best of old song
- Grand theft auto vice city ps2
- Fairy tail comple
- Pompeii 2014 dvd
- Pop dance 2014
- Shriya saran wallpapers
- Men in black 2002 720p
- Space pirat captain harlock
- History of law
- Turn around remix
- Friday night lights saison 1
- Roger Waters 121212
- Nba street 2
- Focus storia wars
- The challenge s25e
- Brave eng subs
- Man woman and the wall
- Yify 1080p star trek
- Ready for the weekend remix nervo
- Skidrow the sims 4
- Extreme music manager
- Lost 3 disco 3 ita
- Independence day dublado
- 2014 dvdrip spider
- The oscar awards
- Pitbull ft christina aguilera feel this moment
- Love rachel set
- Field Notes on Democracy Listening to Grasshoppers
- Super troopers 2001
- Nino d angelo
- X man all
- Life on air
- Three way bangers
- Keith Jarrett Directions
- Crack no cd gta san andreas pc
- Diddy ft usher
- Dark rising 2007
- Footsiebabes dillion harper million ways
- Madea witness protection dvdrip
- Korra episode 3
- The keeper of lost nl
- Unity 3d pro mac
- All over road
- Me mommy and
- Wordpress theme making
- The power within dragonforce
- The hurt locker avi
- The georgia satellites
- The walking dead dutch season 1